Credential Theft Week 1
Our J2 SOC Manager has created a series of pieces around credential theft. In the coming weeks we will unpack several methods of attack. In this, the first in the series, we start with some background information and a dive into attacking passwords in network traffic. Future pieces will discuss other methods and prevention strategies. We hope you enjoy this series and feel free to get in contact us if you have questions, comments or want to further clarity.
In the game of hunting for privilege, it goes without saying that the password is a ‘big five’ target for the threat actor. Just as a hunter knows everything about how a lion moves in action and behaves at rest, a security professional knows how a password might be compromised, and more importantly, how it should be protected. The business owner should expect that the necessary mitigations are in place to make this theft as hard as possible. In this series we’ll discuss credentials, how they might be stolen and how you can make it harder for the criminals to put your administrators head on their trophy wall.
 There are two aspects of the password that interest the attacker and defender. One is the password; the other is its hash. A password hash is a direct one-way ‘fingerprint’ of the password that changes only when the user’s password changes. Depending on the authentication mechanism, either a password hash or a plaintext password can be presented as an authenticator to serve as proof of the user’s identity to the operating system.
There are two aspects of the password that interest the attacker and defender. One is the password; the other is its hash. A password hash is a direct one-way ‘fingerprint’ of the password that changes only when the user’s password changes. Depending on the authentication mechanism, either a password hash or a plaintext password can be presented as an authenticator to serve as proof of the user’s identity to the operating system.
Not all hashes are created equal. Certain cryptographic methods of creating hashes have known flaws. They may be ‘salted’ with an additional password. They may be stored in such a way that the cleartext password can be retrieved. The hash may also be masking a weak password and be easily retrievable.
If the authentication protocol is old enough, the hash can be replayed against other servers or devices without any actual knowledge of the password itself. That means that in some cases the threat actor does not need to know your password, they can use the hash passed around in network traffic or stored on your device.
Windows is loud, by default. By loud we mean angry drunk loud. Everyone can hear it. In technical terms these shouts are called broadcasts. NetBIOS and LLMNR are two examples of an API and protocol respectively that are very noisy and should be disabled by default but are not. The drunk is calling out names and a mischievous passer-by can pretend to be anyone that the drunk is calling. Did you know most browsers broadcast a request when you open them?
 Attacking passwords in network traffic
Attacking passwords in network traffic
Attacking passwords in network trafficWindows will broadcast over multiple legacy protocols and APIs, for a variety of reasons. It may be looking for a network device, it may be a browser request for a proxy server and anyone listening to broadcast traffic can, under certain conditions, ‘pretend’ to be the requested device and dupe the broadcasting device to exchange the password hash. Yes. This can take place in any coffee shop wireless network. Yes, it is enabled by default.
A heavily abused protocol is Server Message Block (SMB). It is typically used for sharing files, printers and client server communications. In most cases the user must authenticate before accessing the service and this process can be abused to collect password hashes. When you mistype a file server address,A heavily abused protocol is Server Message Block (SMB). It is typically used for sharing files, printers and client server communications. In most cases the user must authenticate before accessing the service and this process can be abused to collect password hashes. When you mistype a file server address,your device will broadcast the request. If the destination endpoint has been taken offline and your device can’t connect, it broadcasts the request.
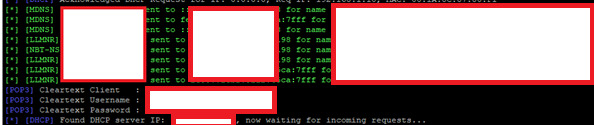
Fig 1. Intercepting a credential hash
A free tool is readily available to listen for these broadcasts. In the image we see that device are requesting the addresses of various servers over several different protocols. If we run the tool in active intercept mode, we can perform a man in the middle attack to force authentication as above. This means we respond as if we are the target.
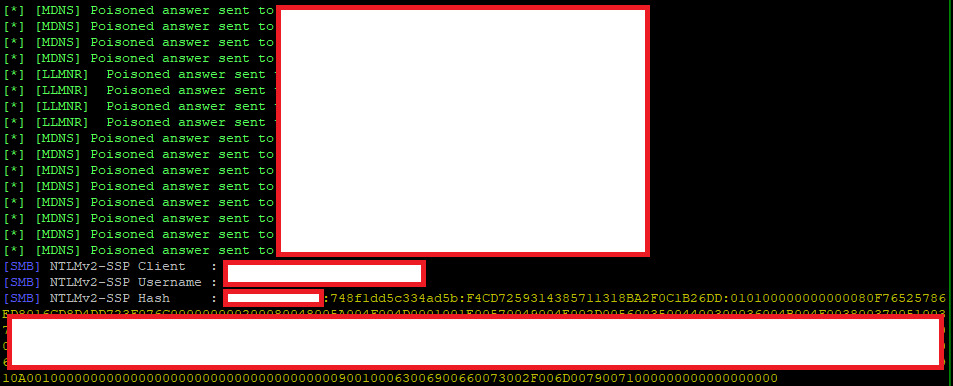
Fig 2: Intercepting a credential hash
One we have pretended to be the target; the victim will reconnect with the password hash as above. This hash may be replayed to other devices for access at the same level of privilege as the user. In this case, the threat actor has no need to crack the hash offline.
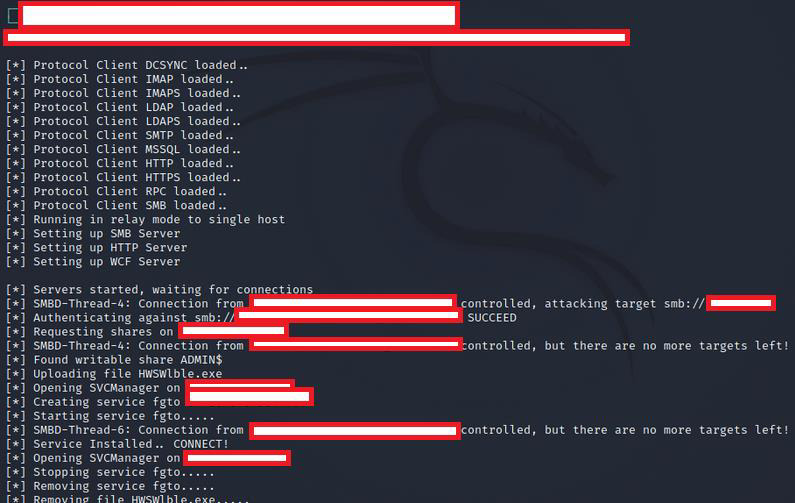
Fig 3. Replaying an SMB credential
There are variants of ransomware that incorporate these remote attack pathways into their code, but this is typically a hands-on process.
There are variants of ransomware that incorporate these remote attack pathways into their code, but this is typically a hands-on process.If this concerns you, make sure you keep checking back for the rest of the series where we will cover more attack methods as well tips on how to detect and prevent credential theft. If you cannot wait that long, get in touch with us today.
J2 Cyber Security
- Hits: 598