South African Insider Risk – What you don’t know will cost you!

This is the second piece in the series around the actual Insider Risk in South African businesses, which follows on from my previous piece on 10 Years in South Africa. I will be going over our real findings on what is really happening within South African businesses. We have analysed actual usage to share information on real risks to educate and provide meaningful advice to identify and then act against these threats.
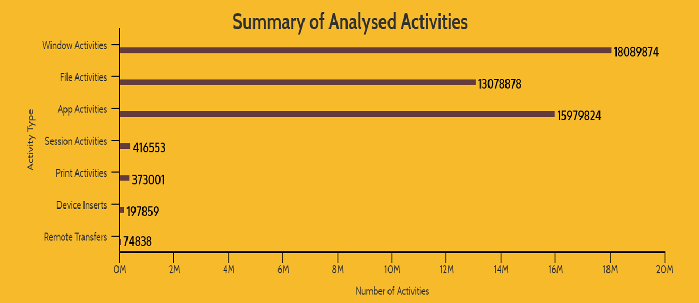
The analysts at J2 Software, using Dtex's SystemSkan Intelligence Framework (SSIF) have looked at over 46 Million Window, File & Application activities along with over 197,000 external USB device insertions to provide you with valuable and accurate information.
The modern business understands that breaches happen no matter what you put in - we will always have gaps - because systems are used by humans and humans have the amazing ability to make unfortunate mistakes.
What we need to ensure is that you have the visibility to instantly identify when a breach has occurred and stop it before there is any lateral movement. We can agree that total prevention is impossible - so identification is critical.
“When defending the end-point from misuse we must apply the thinking that while PREVENTION is better than CURE; DETECTION is better than DISCOVERY - Kevin Halkerd CISSP”
1 in 40 Users Mishandle Information
So let's get down to the facts. When analysing the data - one of the main areas of risk across enterprises is Information Mishandling. The activity identified related to users copying, moving and uploading sensitive and confidential information, including personal and financial information, to unprotected USB devices, local drives and open cloud storage offerings. The risk here is massive - and without the visibility we offered these breaches would not have been detected and likely never be remediated.
It can quickly be calculated that on average 2.5% of the information workforce mishandles information - either by mistake or for malicious purposes. This means that every organisation is at risk. The person sitting next to you could be the one that sinks the ship. That friendly person in Finance who "innocently" copies the Audited Financials to an open Cloud Sharing service - or the line manager who tries to take a copy of the customer database and discount structure before moving jobs to a competitor. We see and stop this every day for our clients - can you do the same?
- I suggest having a look at how long it would take you to notice a breach – research suggests the average is over 220 days (often longer). Please answer these questions and let me know your answers.
- Can you tell me what information was copied to USB drives in the past 24 or 48 hours at your organisation?
Was the data copied to a secure and encrypted device? - Do you know how many files were renamed in the last 7 days?
- Which users placed data of any kind into a cloud sharing service such as Dropbox in the last month?
- What is the total number of new applications installed across your enterprise in the last 14 days?
If you can't answer these questions immediately, how do you expect to be compliant with the most basic security, good governance codes or any information related legislation such as POPI?
- Hits: 2006