South African Insider Risk – Encryption – Why don’t you?

Welcome to the third piece on the South African insider threat landscape which follows on the piece about Employees Mishandling Sensitive Data. In this edition I want to touch on encryption as it appears in South African businesses. Our team have analysed over 47 Million Window, File, Application and File Transfer activities, quickly and accurately, using Dtex SystemSkan Intelligence Framework analytics toolset. We use only real findings to tell you what is really happening within South African businesses.
The modern business should understand that your information is the most valuable asset to people with ill intent, this is far more valuable than the actual laptop or computer it is stored on. We all know and hear about theft from businesses or political offices where the thieves steal only hard drives and laptops. These types of thefts are not after the hardware.
One of the simplest ways to protect these items is with encryption – so we had a look at how much encryption was used around the base. The results were not encouraging; especially when you remember that 1 in 40 staff misuse company data as discussed in my previous post.
 The Results
The Results
We decided to do a quick analysis – both on machine hard drives as well as USB external drives.
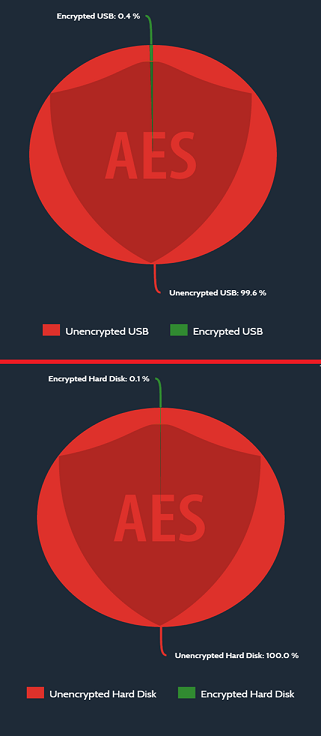
When we looked at the machines themselves we detected that 0.1% of the machines had any form of encryption; this meant that 99.9% of all hard drives under review had their data in plain view – ready to be exploited.
The results were similar with USB storage devices – using data from over 197,000 device inserts it was clear that there was encryption protection on 0.4% of these devices; leaving 99.6% of these totally unprotected.
Where does this leave you?
Consider this for a minute;
- How many USB storage devices, flash drives, etc have you used in your lifetime?
- How easily are these lost?
- How many have you lost?
- Without protection – where is that data now?
- What about the implications of POPI?
These are all questions we should be asking ourselves – why don’t YOU encrypt? Too difficult? Not worth the effort? REALLY?
These excuses hold no water with me; they are just that; EXCUSES. There is a simple method to secure your data on machines and USB even on mobile devices. You can have the visibility of centralised control and management. While you’re at it; we can encrypt the data on your mobile device as well. This will ensure that you have peace of mind knowing that you and your information are protected.
Let’s carry on this conversation – get in contact. Drop me a comment or ask me a question. This doesn’t need to be difficult.
- Hits: 2040