Time for Whale Watching
 Following on with my series on cyber threats, I will briefly touch on Whaling Attacks – also known as impersonation attacks. These attacks are on the increase and entail an attacker impersonating a company executive to force an urgent payment out of the business. I think it is valuable to spend a little bit of time discussing the most common methods. Increasing awareness and providing practical methods to defend against these threats can help make sure you are not next.
Following on with my series on cyber threats, I will briefly touch on Whaling Attacks – also known as impersonation attacks. These attacks are on the increase and entail an attacker impersonating a company executive to force an urgent payment out of the business. I think it is valuable to spend a little bit of time discussing the most common methods. Increasing awareness and providing practical methods to defend against these threats can help make sure you are not next.
Our teams have spent quite a lot of time looking at these types of attacks in recent weeks and I would like to take the time to explain how they normally go down and highlight some simple and practical methods to stop them in their tracks.
I often get asked how the would-be attacker gets their information – and the truth is that it is quite easy. You don’t need to search LinkedIn or other social media channels to get the contacts of the right people within the organisation; just pick up the phone. I will explain below.
As a first step, an attacker will target a business (or businesses) based on their profile or just by pot luck. In a recent attempt one of our customers won a bunch of awards and there was a great deal of hype and press coverage around this, the following day two people were targeted, but the attacker failed.
Now that the target company is acquired a quick search allows the attacker to get the first part of the information they need, this is usually the CEO, CFO, etc. They now have the name of their Whale.
The next step is to identify the target to approach within the business. This can be done with a simple telephone call. Our attacker calls the office and tells the friendly receptionist that they are from Acme Inc. (or any made up business) and need to urgently send the Accounts Receivable manager a proof-of-payment for an overdue account. The helpful receptionist will almost always give them the required information. Armed with name and email address we are ready to go.
Using a fake and free email account they begin. A simple display name change is all that is usually required. The opening email is usually a greeting and enquires about the target and their availability. This opening email is also used to create the Whale’s identity to the attacker in conversation.
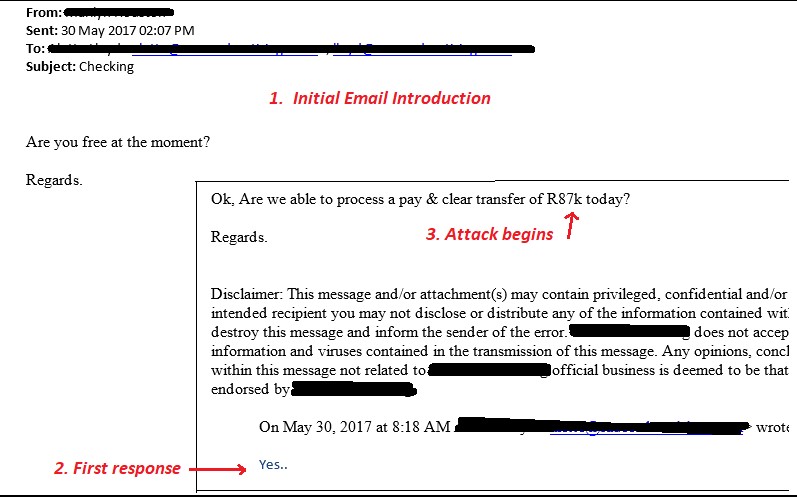
After the initial response the Whale usually jumps right to it. The email requests an urgent payment and stresses the importance and places pressure on the unsuspecting target. This may take two or three replies to get bank details, amounts and the reason for payment. The target is always told they must act quickly.
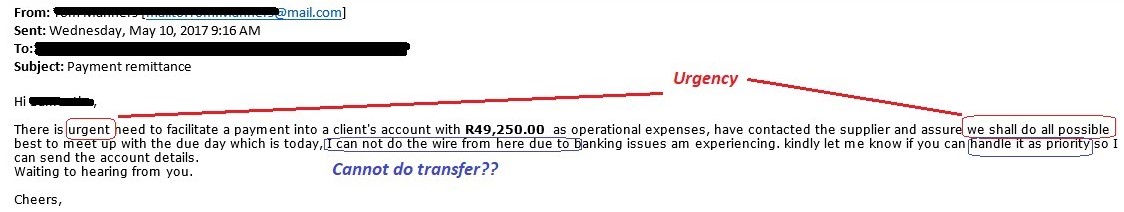
Often this happens when the MD is out of the office, which is also easy to find out.
The compliant staff member often does as they are instructed. Payment is made into the attackers account and the funds are cleared.
The entire attack is very simple to do and can be completed in less than an hour at virtually zero risk. These attacks are often successful as the victim wants to complete the task for their employer.
This makes it very attractive to cyber criminals.
In the electronic world we find ourselves in, these attacks are inevitable and there are some very simple methods to prevent this from happening to you. These are all part of the layered approach to security required in the modern world.
- Policy – as with most advice, the first step is policy. Make sure that staff have a policy to follow in order to approve a payment, especially urgent payments.
- Awareness – staff awareness is critical to prevent this attack. The language of the emails, tone and communication style of your CEO is difficult to copy. Look out for mistakes.
- Security Measures – besides the human factor make sure you deploy a targeted threat protection solution to ensure that external email address are highlighted and spoofed emails are blocked before they even get to your end users.
It is important to note that people are a very important part of your security strategy. I am also happy to have a chat around this and other risks to improve your security standpoint.
Please feel free to engage and add to the conversation so we can spread the word to help with the good fight. In the world of growing cyber threats, when we increase awareness and share intelligence we all win.
- Hits: 1748