Petya – Pet yourself
Barely a month after the WannaCry outbreak and announcement of Fireball, the globe is under attack once more. The only really exciting part is watching the researchers agree with a name.
I am almost certain you are growing weary of InfoSec professionals knocking at the door, clogging up your feeds and telling you the same thing. If you had patched this or fixed that or prevented these.....
It is not that helpful now. Don’t you hate it when everybody states the obvious? Me too!
The “it won’t happen to me” attitude will not help you either – nobody is immune to attack. The reports are all talking about Ukraine, Europe, India, but we have reports of South African business being hit too. These is not only companies associated with international owners; these are home grown South African businesses. We live and co-exist in a global, connected world.
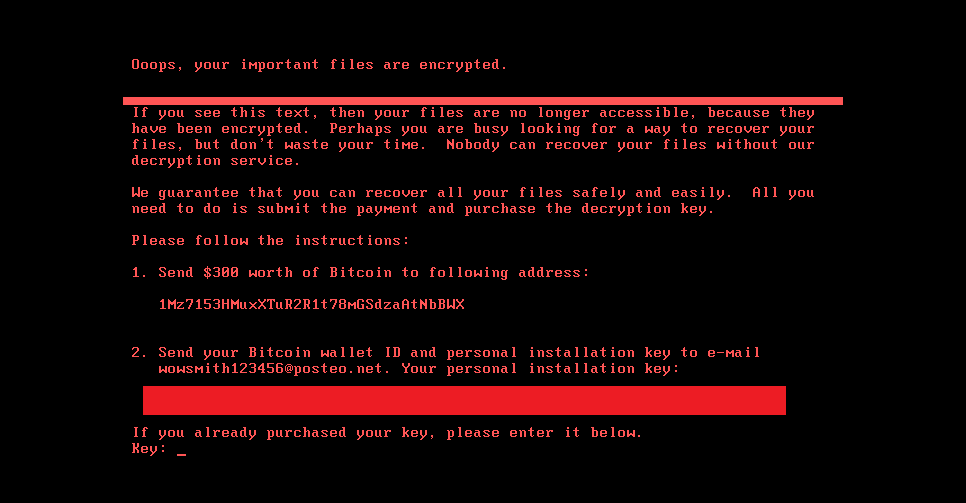
The reality is that Petya or NotPetya or Goldeneye or whatever you want to call it uses an old vulnerability to spread itself. There are reports of no Command and Control activity and it takes over the Master Boot Record – restarts itself and makes your machine and anything connected it inaccessible. Let us dwell on this for a second, no C&C activity – this is automation of malware delivery. A new variation on an old piece of code.
The attackers are innovating. Why aren’t you?
There are relatively simple methods of preventing this from happening to you, sure. Then why has it affected hundreds of thousands of machines? Do you really think that security is too expensive to do well? Ask the business who cannot trade for 2 days or the executive who has lost 3 critically important documents that they saved only on their desktop.
User awareness may be on the increase, but if you allow the delivery of a malicious attachment without properly scanning it and stopping it – It is your fault.
If you haven’t patched the SMB (Eternal Blue) exploit – it is your fault.
If you cannot detect lateral movement activity at the end point – it is your fault.
The next question is, do you even know what vulnerabilities you have across your environment? We are sitting today fighting an ever changing threat landscape and we still see so many organisations that are doing nothing about it.
I urge you to have a chat to me. I encourage it. I do not think you know how easy it is to protect yourself. We cannot protect you from everything out there – nobody can. We strive to improve your visibility and massively reduce the risk. You need visibility now.
We know the changing threat landscape is overwhelming so let us help be the change. I am happy to be the “bad-guy” and introduce simple security measures which will greatly reduce your risk.
Ongoing, persistent and non-intrusive security monitoring is your best defence. Rapid reaction and pro-active remediation will mean that your users are working. Do nothing and they will be sitting at home, enjoying their time off while you struggle to get your environment back up.
More discussions leads to more discussion. More talk about what needs to be done leads to nothing actually being done. So let us take action. As a thank you for reading this to the end, get in touch with me – via our website or here – and we will provide you a 25% discount on the J2 CSC Cyber Risk Assessment.
Take action – pet yourself.
- Hits: 1460