Out of Office
It is that time of the year again, when annual leave is being cashed in for some relaxation and holiday fun.
As you know, hackers don’t take leave, this time of the year can provide them massive pay days if your defence mentality goes on holiday. The holidays are a lucrative time of year for the cyber attacker. Festive season online shopping has their malware busy, be sure not to add to their ever-growing gift pile.
The out-of-office automated emailer may seem like the right thing to do, you know, so that clients or co-workers emailing you will know that you are out of office. However, think long and hard about what sorts of information you provide in your response. As with unsolicited calls and emails, you must never give any information that the person on the other side does not need to know. This can pose a massive security risk.
These seemingly harmless automated replies can potentially reveal large amounts of sensitive data about you to anyone.
Think about what you would put in your out-of-office mail. Does it resemble the example below?
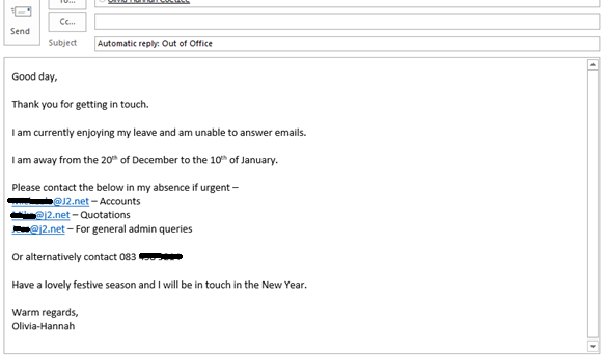
The information in this response is like gold in the hands of the cybercriminal, inside information can lead to a successful breach.
Having the exact dates of leave can lead to impersonation attacks and the information you have provided can be used in social engineering efforts to gain a foothold. In the response above, the attacker will know when you are away and who else in the organisation can be targeted while you are gone. Don’t make it that easy.
As part of your cyber security awareness training program you must ensure that your people understand social engineering and how the cybercriminals can use a small piece of information to begin the breach.
J2 Software offers awareness training and incorporates the Mimecast Ataata interactive awareness training to engage the user. It does not help to simply sift through theory or non-entertaining video content that takes hours to complete – this is not effective. By presenting real life scenarios and leveraging phishing simulations we can teach your team what they need to look out for. Engagement, knowledge and awareness are your magic potion to get the end user to be the first line of defence in your organisation.
A single point solution will not help fend off cyber-attacks. You require a comprehensive and integrated program, made up of numerous layers to reduce risk. Understand that individual layers will fail, but with the right foundation in place you can remain secure by understanding what is normal. When you know what normal is, identifying anomalies is far easier and keeping yourself compromise free can be a reality.
Having the right email security in place is crucial, ensuring that this is managed as part of your overall cyber security defence program is more important.
When setting an out of office emailer, rather keep it to the bare minimum, keep it vague, the people you know already have ways to contact you if they need to.
Remember that any information shared, online or physically, can be used in a cyber-attack. Let us help you become cyber strong to build a bigger, better and safer 2019!
Let’s get real.
Olivia-Hannah Coetzee
- Hits: 1437