Scammers are after you…
The number of cyber-attacks are increasing and the cyber crime syndicates will use any method possible to get you to part with your hard earned money. They are after sensitive data, credit card information and “facilitation fees”. Every single person is a target and rest assured that the cyber criminal does not discriminate.
In this piece I will speak about the use of social media to kick off a cyber attack. I will use a real example that we encountered this week and it is important to note that these types of attacks happen across all platforms. Older people are also seen as soft targets because the criminals rely on their trusting nature and limited knowledge of the new digital world we live in.
The steps in this type of attack follow the same pattern:
- Trust - The first step is to establish trust and the attacker will engage in conversation, often with a breached account of a friend on something like Facebook or establishing a connection on LinkedIn.
- Question - Once the trust is earned there is a question, this is done in order to make it appear like you may have missed something.
- Fortune - The next step is to then tell you about their amazing fortune, this can also be the time that you are made an offer you should not refuse.
- Introduction – Now that the victim is on the hook, the criminal introduces you to a third-party that will be your agent. This agent will then facilitate the transaction. Their profile will be full of photos of money and “prize winners”.
- Payment – Having covered the previous steps the criminal syndicate will extract the information and money they want until you realise that you have been fooled. This will start with a small facilitation fee or courier fees – either via a transfer or by providing your credit card details. You may also be asked to provide login credentials or other sensitive and personal information. The costs will continue until you stop paying them. It is at this point that they will disappear.
The example we have here happened on Facebook, using Messenger. The victim is a 70-year-old lady and the attackers used a Facebook friend’s compromised account to launch the attack. I am happy to say that no senior citizens were harmed in this attempt.
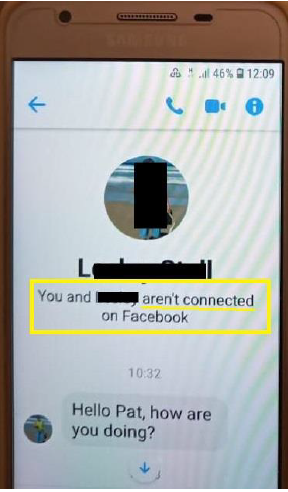
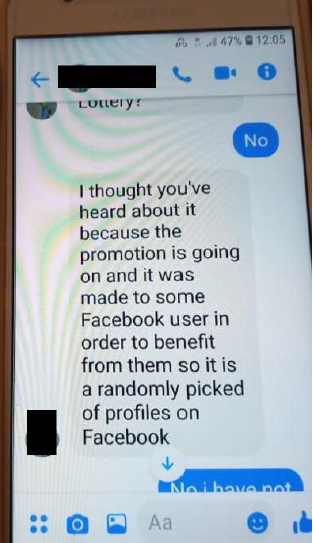
The message comes from an existing friend on Facebook. In this case the account was copied as you can see from the highlighted area of the message. Attackers will use compromised accounts or simply create copy-cat profiles.
A standard response leads the attacker to ask whether you have heard about the lottery (or another offer) that is being run.
Question
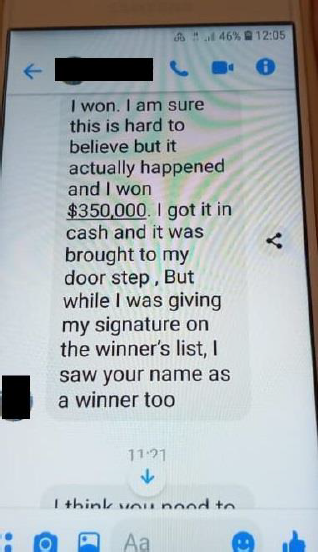
The attacker then tells you about this amazing (too good to be true) promotion. This is aimed at sparking your interest because it might seem plausible, especially to those that may be desperate.
Fortune
The attacker will now go to tell you about their amazing luck. They have received this massive payout and amazingly they saw your name on the winners list.
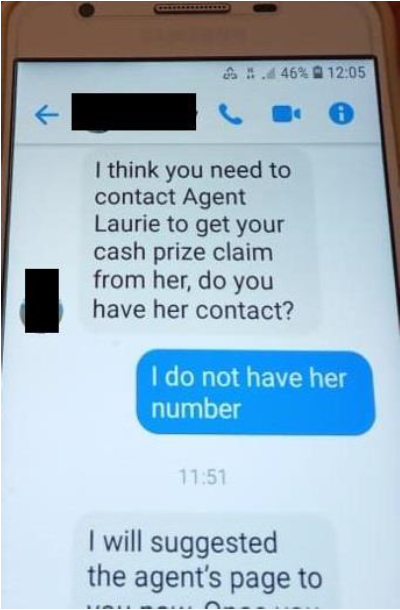
Introduction
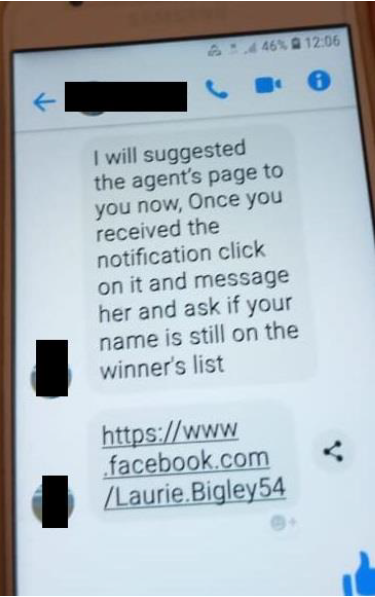
Creating some excitement, the attacker now introduces you to the agent. There is a call to action and you must act soon in order to see if you are still on the winners list.
Payment
Looking at the “agent’s” profile, there are a lot of pictures of large sums of money and also images showing people who have WON in the promotions.
If you do not take a second look at the picture, maybe you will miss how the Logo has been superimposed on the image. The date has been manipulated, the currency is changed and the signature section is not aligned to the big cheque either.
Is it not long before the request for sensitive data, login credentials, credit card details or payment of the facilitation fee takes place…..
Please take care out there and whenever you are contacted unexpectedly or offered something which appears to be life-changing, verify and do not give any confidential information to anybody over a messenger or the telephone.
Apply common sense in these situations and think about the situation in the “real-world” – would you trust a person who comes out of nowhere and offers you $350,000.00 in cash? Why would this be different in a cyber space.
If you need any advice or wish to add to this information, please get in touch with me. I am always happy to discuss real and practical methods to remain cyber secure.
#Letsgetreal
John Mc Loughlin
#J1TopTip
- Hits: 1478