They’ve Stolen Your Session & Credentials
A few weeks ago there was yet another (one of hundreds) of attempts to get me to take the bait. With the help of Jaiden in our Cyber Security Centre (#J2CSC), we went a little deeper to give you a view on what happens when these emails hit you and your people. Without a combination of a layered email resilience programme, effective user awareness and correct configuration of machines and user privilege you could be on the wrong end of a successful credential theft crime gang.
The email came is as an apparent link to a Mutual Non-Disclosure Agreement. There was nothing else attached to the email and basic systems would never stop this from hitting your people’s inbox.
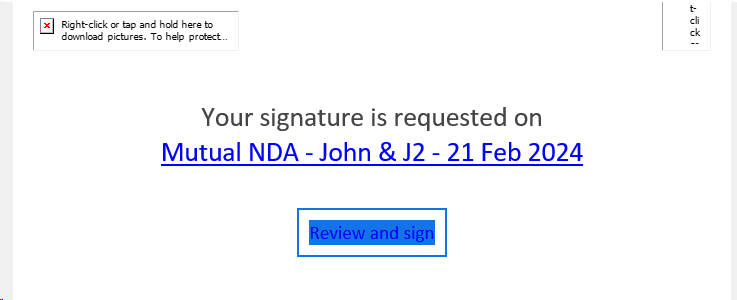
When the user clicks on the link to the “document” they would be taken on an online trip that jumps from a fake Single-Sign-On (SSO) page (https[:]//sso[.]college[/]johnl…) that will load and then redirect you to the legitimate “login.microsoft” page with a Cookie Error (it does this even if cookies are enabled).
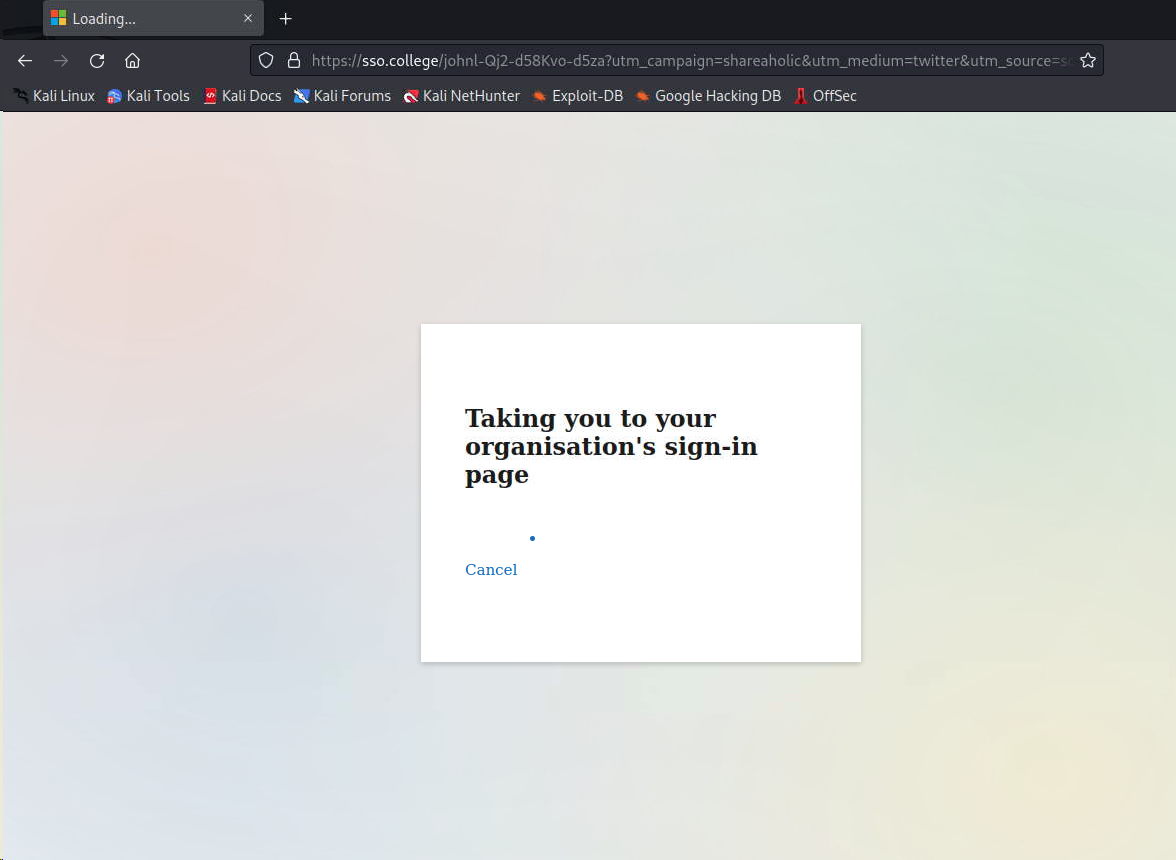
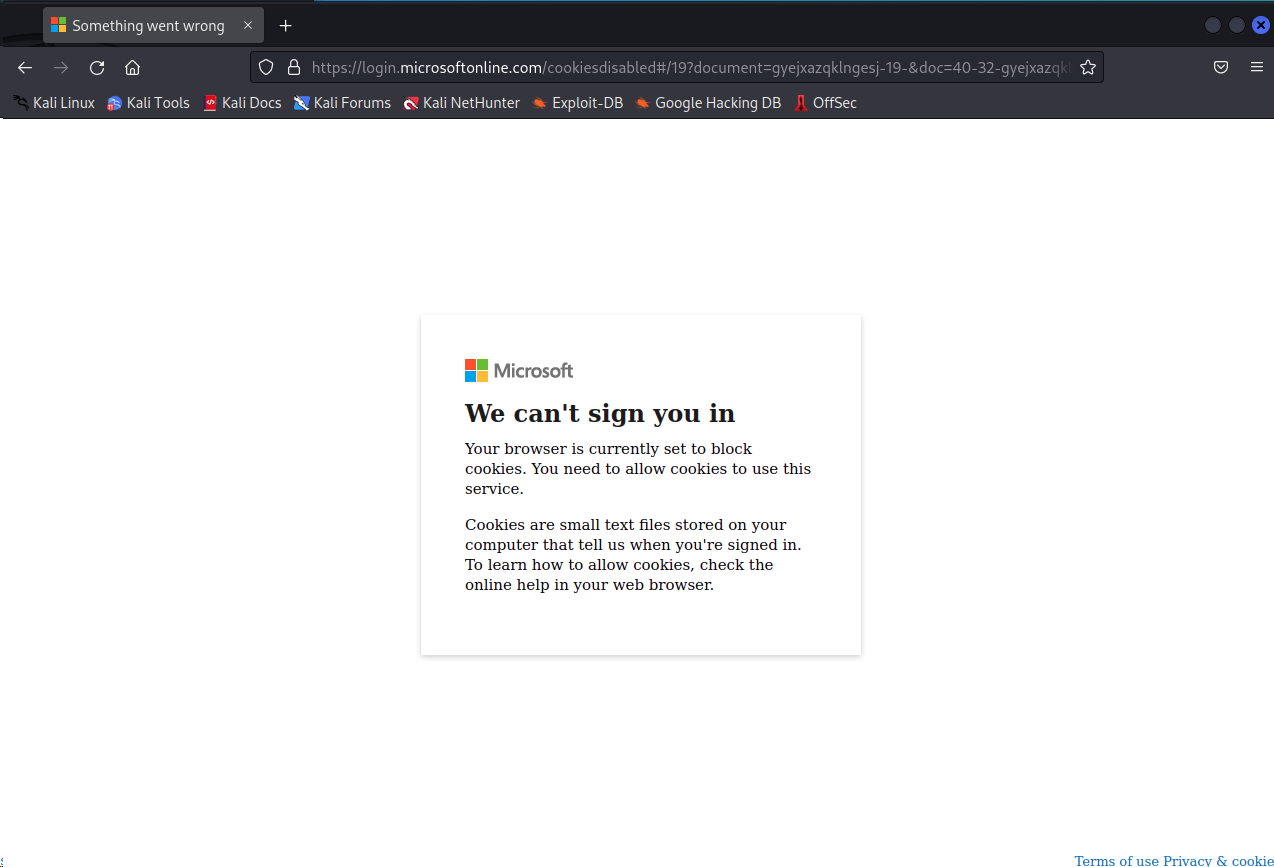
Jaiden pointed out that during this re-direct process we were never prompted to input our credentials at any point. This indicates that the attackers intent was to steal whatever data was freely available during the redirect process from memory and/or steal the session token. When targeting Session Tokens the attacker then replays this and essentially tricks the system to believe that it is you – thus giving them total control and access. You and your user would just think that it didn’t work and continue their day without knowing they had been compromised.
You also had the option presented that would allow you to Delegate the signature responsibilities to someone else.
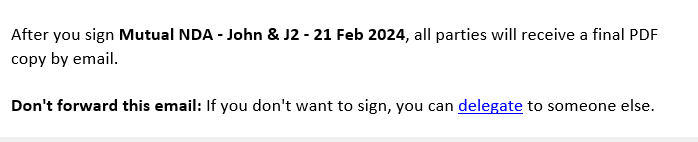
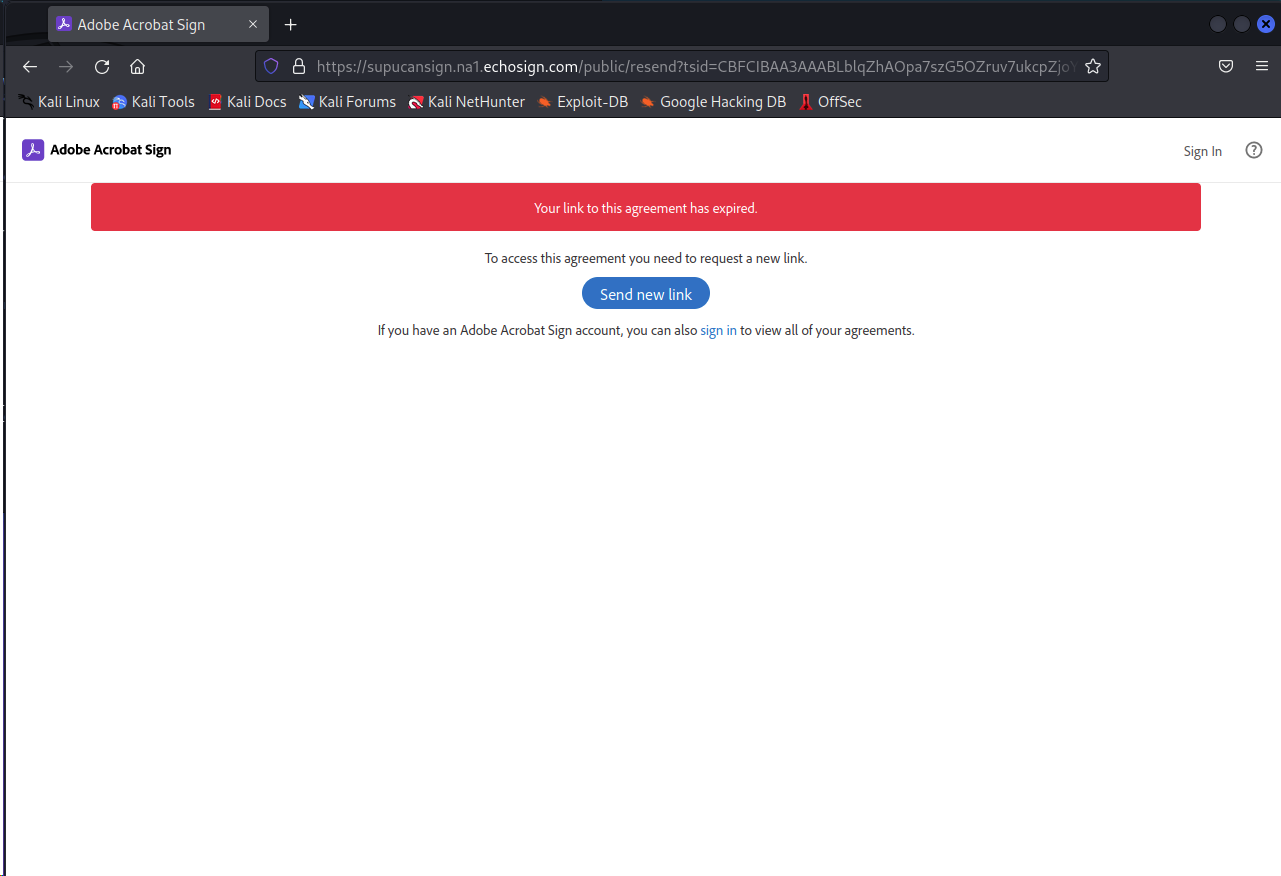
Upon clicking the “delegate” link within the email, you would be taken to what appears to be a legitimate (though depreciated) page from Adobe (echosign.com was an official site used by the Adobe cloud suite but has since been replaced by adobesign.com). The legitimacy of this link was confirmed with other sources.
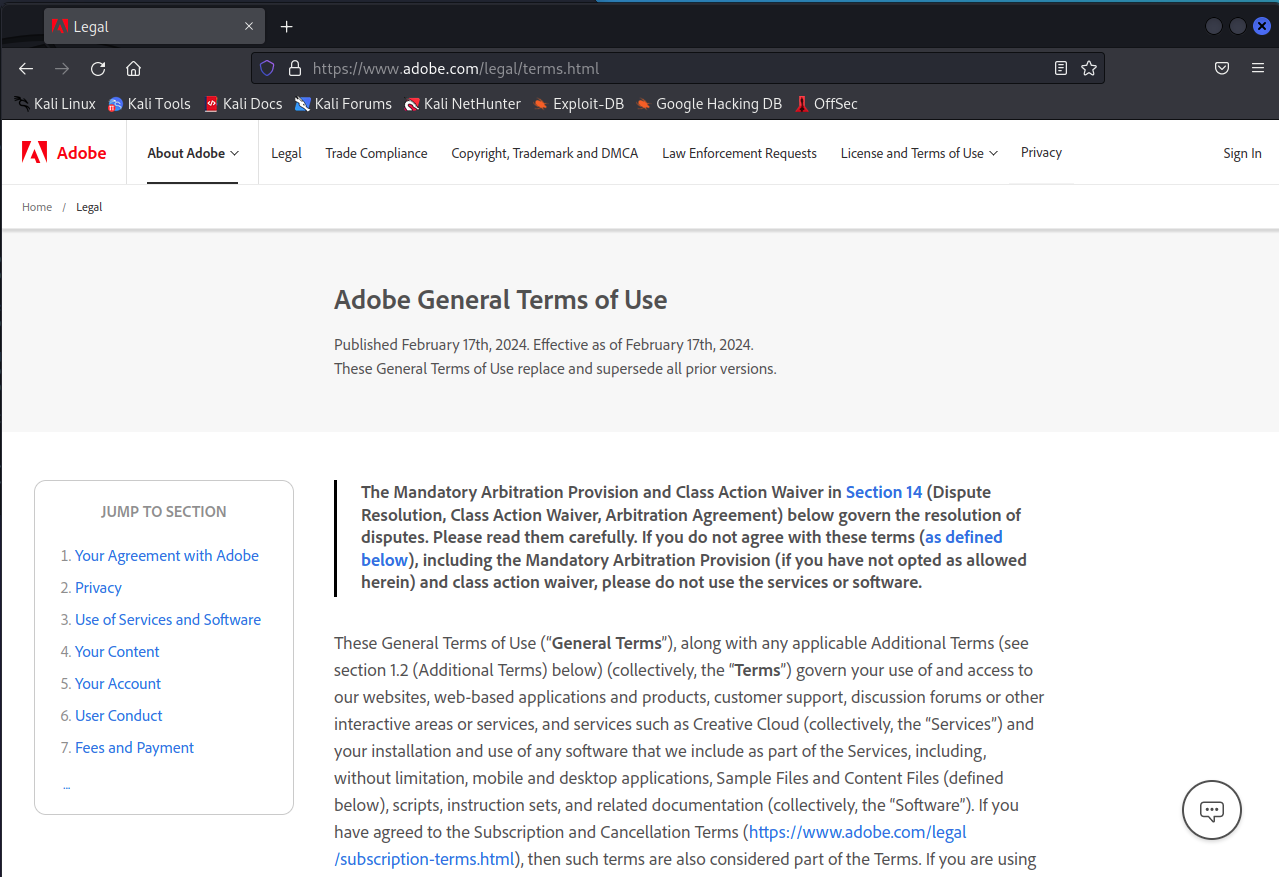
The attackers do make use of legitimate information where applicable to reduce suspicion, the link on the signing page for example goes to the real terms of service from Adobe’s website.
The attackers often look to steal session tokens and other data that is live on the machine to get into your cloud systems. This would give them time to trawl your data and without the correct resilience programme controls, you would not even know that they were there. It is tantamount to having an intruder in your home that you cannot see.
The attackers often look to steal session tokens and other data that is live on the machine to get into your cloud systems. This would give them time to trawl your data and without the correct resilience programme controls, you would not even know that they were there. It is tantamount to having an intruder in your home that you cannot see.
How do we stop this from happening to you:
- Make sure there is a solid and comprehensive cyber resilience programme running within your business.
- Deploy an effective User Awareness Programme that drives knowledge, is entertaining and engaging.
- Speak openly about Standard Operating Procedures, if something doesn’t look or feel right, question it, verify it and think before you act.
#letstalk about the effectiveness of your Cyber Resilience Programme.
Until the next time.
John
- Hits: 3621